They pop up on your screen, warning you that your computer system is infected with all kinds of viruses and offer to help you remove them.
Some mimic actual system notices to leverage the trust you have in your legitimate security software, so you go ahead and click.
By clicking it you opened the door to malware and, potentially, a host of other dangers. You’ve been had!
Those pop up messages contain “scareware”, fake or rogue anti-virus software. Malicious applications posing as antivirus software are not new, they’re increasingly more sophisticated and constantly challenge legitimate AV software.
“But, but, I have AV software! The best, recommended by Bonza….”
It’s important to understand: there is no anti-virus protection that will detect 100% of the threats out there on the World Wide Web. The point of anti-virus protection is to minimise the risk of your computer becoming infected.
Don’t fall into the trap of believing security software (including ESET Smart Security) offers automatic protection from everything and therefore you no longer have to think, participate, control, what you click on or download. Anti-virus can’t catch everything, even with advanced heuristics like ESET.
You must stay eternally vigilant!
If you’re faced with any of the warning signs of a scareware scam or suspect a problem, shut down your browser.
Don’t click “No” or “Cancel,” or even the “x” at the top right corner of the screen. Some scareware is designed so that any of those buttons can activate the malware.
If you use Windows, press Ctrl + Alt + Delete to open your Task Manager, and click “End Task.”
If you use a Mac, press Command + Option + Q + Esc to “Force Quit.”
Make it a practice not to click on any links within pop-ups.
Bonza recommends that you take precautions to ensure your operating systems and patches are updated and your legitimate security software is current. If you receive anti-virus pop-ups, close the browser or shut down your computer system. Run a full anti-virus scan when the computer is turned back on.
How to spot a fake?
1. You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry;”
2. You may get “alerts” about “malicious software” or “illegal pornography on your computer;”
3. You may be invited to download free software for a security scan or to improve your system;
4. You could get pop-ups that claim your security software is out-of-date and your computer is in immediate danger;
5. You may suddenly encounter an unfamiliar website that claims to have performed a security scan and prompts you to download new software.
What to do to minimize the risk of a malware attack?
To significantly minimize your risk of infection routinely perform an On-demand computer scan.
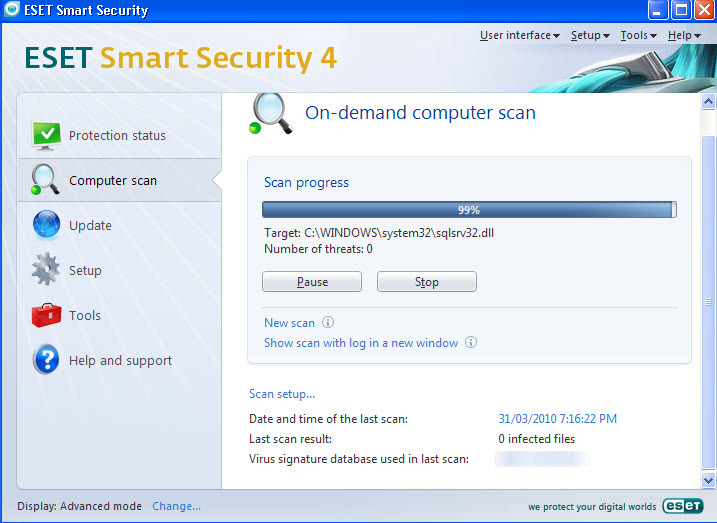
Know what your protection status means. The ESET icon next to the system clock will stay green as long as maximum protection is ensured. If it turns yellow, maximum protection may not be ensured and, if it turns red, maximum protection is not ensured.
BAD STUFF DEFINITIONS
Virus
A Virus is a program that is activated by attaching copies of itself to executable objects. Viruses can reach your computer from other infected computers, via data medium (CD, DVD, etc.) or through a network (local or Internet). There are several types of viruses:
File viruses: File-infecting viruses attack executable programs, such as all files with “.exe” and “.com” extensions.
Script viruses
Script viruses are a subset of file viruses, written in a variety of script languages (VBS, JavaScript, BAT, PHP, etc.). They either infect other scripts (e.g., Windows or Linux command and service files), or form a part of multi-component viruses. Script viruses are able to infect other file formats, such as HTML, if the file format allows the execution of scripts.
Boot viruses
Boot viruses attack boot sectors (removable media boot sector or hard disk master boot sector) and set their own loading routines at start-up.
Macro viruses
Macro viruses attack documents where other commands (macros) can be inserted. These viruses are often imbedded within word processing or spreadsheet applications, since macros are easily inserted into these types of files.
Viruses can also be classified according to the way they perform their action. While direct action viruses perform an action immediately after the infected object is activated, resident viruses stay and work in the computer’s memory.
Worm
A worm is an independent program that replicates its copies across the network. Unlike a virus (which needs the infected file to be copied in order to replicate itself), the worm spreads actively by sending copies of itself via LAN or Internet, email communication, or through operating system security bugs.
They can also bring with them additional malware (such as installing backdoor programs), though this behaviour is not strictly limited to worms. Worms can cause a great deal of damage–often they are used to “jam” communication channels by means of a DoS attack. A worm is capable of spreading worldwide, via the Internet, in minutes.
Trojan
A Trojan is a malware program that, unlike viruses or worms, cannot copy itself and infect files. It is usually found in the form of an executable file (.exe, .com) and does not contain anything aside from the Trojan code itself. For this reason, the only solution is to delete it.
Trojans have various functions–from keylogging (they log and transmit every keystroke), to deleting files or disc formatting. Some contain a special feature that installs a backdoor program–a client-server application that grants the developer remote access to your computer. Unlike common (legitimate) software with similar functions, it installs without the consent of the client computer.
Adware
Adware is short for advertising-supported software, which is software dedicated to displaying advertisements. Adware works by displaying pop-up windows during Internet browsing, by setting various websites as your homepage or by opening a special program interface window.
Adware is often installed bundled with free-to-download programs, and the client is usually informed of this in the End User License Agreement. Adware advertisements allow freeware developers to earn revenue by offering program features available only with the paid version. In most cases, installation of adware falls within legal guidelines–there are many legitimate advertising-supported programs. However, issues such as the assertiveness of advertisements as well as their content can make the legality of some adware questionable.
Spyware
Spyware is software that uses the Internet for collecting various pieces of sensitive information about the user without his/her awareness. Some Spyware programs search for information such as currently installed applications and a history of visited websites. Other Spyware programs are created with a far more dangerous aim: the collection of financial or personal data for the purpose of Identity Theft.
Riskware
This type of malware includes all applications that increase the user’s security risk when running. As with spyware and adware installation, riskware installation may be confirmed by license agreement. “Dialers” are a common example of Riskware–programs that divert connection to a preset paid number. Such programs can be legally used for Internet service payments, but they are often misused and the diverting occurs without the user’s awareness.
Dangerous applications
A dangerous application is the term used for legal programs that, though installed by the user, may subject him/her to security risks. Examples include commercial keylogging or screen capture, remote access tools, password-cracking and security testing programs.
Hoax
A hoax is deliberate misinformation sent by email, and they are spread with the help of an unsuspecting or uninformed public. Hoaxes are typically designed to get a user to do something they should not do. Malicious hoaxes often advise users to delete valid operating system files, claiming that the file is a dangerous virus.
In many cases, hoaxes refer to a credible institution/company in order to gain the reader’s attention. For example, “Microsoft warns that…” or “XXX announced”. These messages often warn of disastrous or even catastrophic consequences. The warnings have one thing in common – they urge users to send the messages to everyone they know, which perpetuates the life-cycle of the hoax. 99.9% of these types of messages are hoaxes.
Hoaxes cannot spread by themselves, the only way to protect yourself is to verify the authenticity of an email message before taking any action.
Scams
Scams are deceptions perpetrated on computer users for the purpose of financial gain or identify theft. One of the most common scams involves an unsolicited fax, email, or letter from Nigeria or other West-African nation. The letter will appear to be a legitimate business proposal, but will require an advanced fee from the target. The proposal is of course fraudulent, and any fees paid by the target are immediately stolen.
Another common form of scamming includes phishing email messages and websites. The purpose of these scams is to gain access to sensitive data such as bank account numbers, PIN codes, etc. Access is usually achieved by sending email masquerading as a trustworthy person or business (financial institution, insurance company).
The email (or website that the user is directed to) can look very genuine and will contain graphics and content that may have originally come from the source that it is impersonating. The user will be asked to enter personal data such as bank account numbers or usernames and passwords. All such data, if submitted, can easily be stolen and misused.
It should be noted: banks, insurance companies, and other legitimate companies will never request usernames and passwords in an unsolicited email.
Tags: computer security threats, ESET, ESET anti-virus software, ESET NOD 32, ESET Smart Security, fake anti virus popups, fake anti virus software, fake security popup, fake virus warnings, malware, rogue anti-virus software, scareware
|
This entry was posted
on
Sunday, April 4th, 2010 at
12:43 pm and is filed under
Computer Problems . You can follow any responses to this entry through the
RSS 2.0 feed.
Both comments and pings are currently closed.
|

 Published
April 4th, 2010 by
Roslyn Garavaglia
Published
April 4th, 2010 by
Roslyn Garavaglia 